Your download url is loading / ダウンロード URL を読み込んでいます

Your download url is loading / ダウンロード URL を読み込んでいます
Course of Manufacturing firms are continuously scrutinized to stick to the very best and most secure office requirements. The Occupational Well being Administration (OSHA) performs a key function within the enforcement of security pointers and when firms have incidents, the fines can run as much as hundreds of thousands of {dollars}. OSHA has outlined requirements corresponding to Course of Security Administration (PSM) that assist firms establish, management, and mitigate security dangers.
PSM knowledge to foretell threat
Course of security knowledge is locked in many various sources and are a mixture of structured, unstructured, static, and dynamic info. Pankaj et al, present the next overview on this – Determine 1. After we have a look at this overview, it’s straightforward to see the assorted attributes for BIG knowledge, additionally referred to as the 7 V’s.
These 5 particular use instances will finally be expanded by IBM and also will be made out there to the ecosystem for enlargement by particular person corporations and/or distributors. And though these Cloud Paks are optimized to run on the IBM Cloud, as a result of they're constructed on prime of OpenShift they can run on just about any cloud basis, making a no-lock-in answer that must be extra palatable to corporations who aren't IBM-centric or unique.
With Course of knowledge qualifying as “BIG” knowledge, combining these supply fashions will be constructed for predictive evaluation. One space that this can be utilized for is threat evaluation. The researchers on this case have described totally different layers of threat, all interconnected and reflecting the ability. Every layer makes use of totally different enter sources – which ends up in a threat classification. Contemplating the frequency of occasions taking place on the facility, a method was established to find out the chance profile extra precisely for a given state of affairs – on this case the chance of a mud explosion. The developed threat framework for Massive Knowledge is displayed in Determine 2.
Machine Studying to attain larger situational consciousness
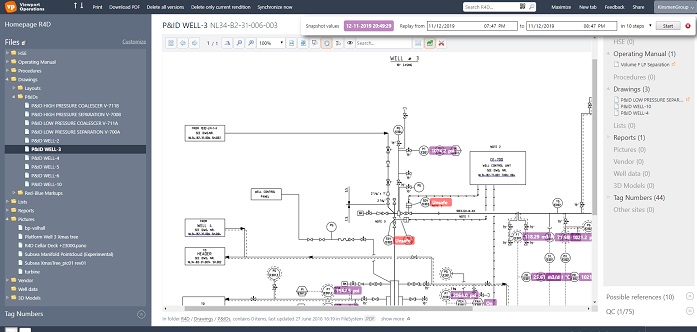
Subsequent to predictive analytics, the big knowledge set can be used to supply operators with a a lot larger situational consciousness. It’s straightforward to ascertain that the various totally different knowledge sources can produce conflicting info for facility operators that in case of emergency want to reply in cut up seconds. Offering facility operators with all of the correct info out there within the underlying sources will be trivial to stopping incidents within the facility.
Software program options exist that analyze the underlying knowledge sources and discover hidden patterns that enable the linking of knowledge in methods normally not out there. Using advanced doc extraction strategies, mixed with sample matching and machine studying, the software program can make the most of all knowledge sources in an effort to hyperlink to the information. When a facility operator opens a doc, he has rapid visibility into the historic knowledge, referenced tools manuals, present and historic work orders and rather more, see Determine 3.
Many alternatives exist for utilizing BIG knowledge applied sciences in manufacturing. Whereas some are nonetheless in a analysis part, others are within the type of usable merchandise that provide price efficient approaches for small and huge organizations.